In today’s digital landscape, protecting sensitive data, particularly Protected Health Information (PHI), is crucial for healthcare organizations. With strict regulations like HIPAA in place, having the right software to identify and secure PHI is essential. This article explores various software solutions designed to find and safeguard PHI effectively, their importance, types, key features, and best practices for implementation.
“Software that can find protected health information (PHI) includes data loss prevention (DLP) tools and electronic health record (EHR) systems, which scan for and help protect sensitive health data.”
In this article, We will discuss “ software that can find protected health information”
What is Protected Health Information (PHI)?
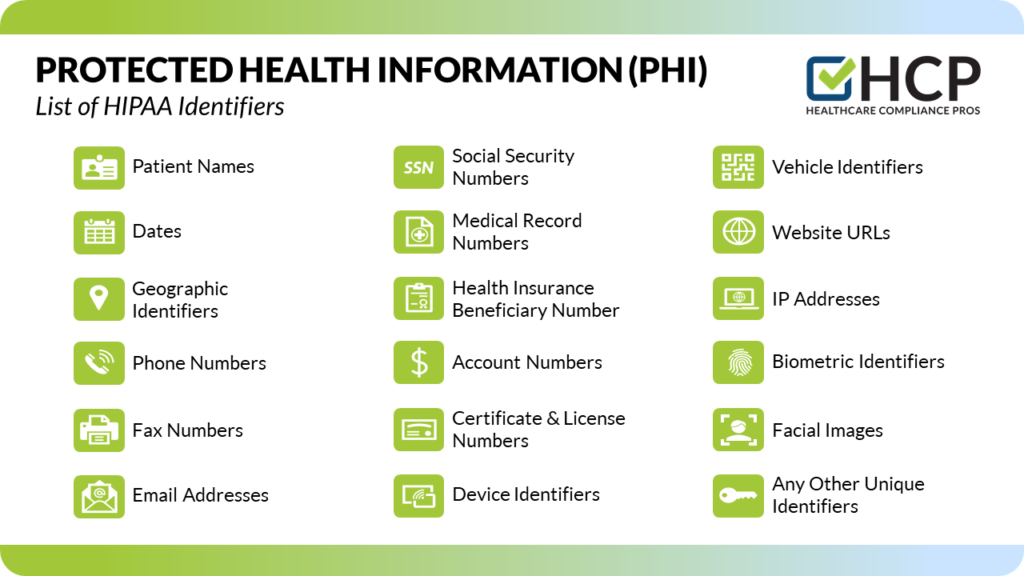
Protected Health Information (PHI) refers to any individually identifiable health information that is created, received, stored, or transmitted by healthcare entities. This includes names, addresses, dates of birth, medical records, treatment histories, and any other information that could potentially identify an individual. Due to its confidential nature, PHI is subject to stringent regulations aimed at protecting patient privacy. Understanding what constitutes PHI is the first step in ensuring compliance and safeguarding sensitive data.
Why is It Important to Find PHI?
Finding and protecting PHI is critical for several reasons:
- Regulatory Compliance: Healthcare organizations must comply with regulations such as HIPAA to avoid severe penalties, including fines and loss of reputation. Non-compliance can lead to legal actions and costly settlements.
- Data Breach Prevention: Identifying PHI helps prevent unauthorized access and potential data breaches, which can compromise patient trust and lead to significant financial losses. Cyberattacks targeting healthcare data have been on the rise, making it essential to safeguard PHI.
- Patient Trust: Safeguarding sensitive information fosters trust between patients and healthcare providers. Patients are more likely to share their information if they believe their data is handled securely, which ultimately leads to better patient outcomes.
- Operational Efficiency: By locating and managing PHI effectively, organizations can streamline their operations, reduce redundancies, and enhance data management practices. This can lead to improved workflows and better resource allocation.
Types of Software That Can Find PHI:
Several software solutions can effectively identify and protect PHI within healthcare organizations. Here are some of the most common types:
Also Read: Why Is Sid Changing For Rubrik Software Restore Ad – Understanding Rubrik’s SID Management!
1. Data Loss Prevention (DLP) Tools:
DLP software monitors data movement and usage to prevent unauthorized access or sharing of sensitive information. These tools can scan emails, documents, and databases for PHI, helping organizations maintain compliance and reduce risk. DLP solutions often include features such as:
- Policy Enforcement: Automatically apply policies regarding the handling of PHI.
- Incident Response: Generate alerts when PHI is accessed or shared inappropriately.
- Content Discovery: Identify sensitive data across various storage systems and devices.
2. Electronic Health Record (EHR) Systems:
Many EHR systems include built-in features to identify and manage PHI. These systems often have compliance tools that ensure sensitive data is appropriately stored and accessed only by authorized personnel. Key features may include:
- Audit Trails: Track who accessed PHI and when, allowing for accountability and monitoring.
- Role-Based Access Control: Ensure that only authorized users can access specific types of PHI.
- Data Encryption: Protect PHI during transmission and storage to prevent unauthorized access.
3. Compliance Management Software:
This software assists organizations in managing compliance with healthcare regulations. It often includes features for monitoring, auditing, and reporting on PHI, helping organizations identify potential vulnerabilities. Benefits of compliance management software include:
- Regulatory Updates: Stay informed about changes in regulations affecting PHI.
- Policy Management: Streamline the creation and distribution of policies regarding PHI handling.
- Training Management: Ensure staff are trained on compliance procedures related to PHI.
4. Data Discovery Tools:
Data discovery software scans databases and file systems to identify unstructured data containing PHI. These tools help organizations locate sensitive information across various platforms and ensure it is adequately protected. Important features of data discovery tools include:
- Automated Scanning: Schedule regular scans to identify and classify PHI.
- Data Classification: Categorize data based on sensitivity levels to prioritize protection efforts.
- Reporting Capabilities: Generate reports on the location and status of PHI for compliance audits.
5. Risk Assessment Tools:
These tools evaluate the security posture of an organization and identify areas where PHI may be at risk. They help organizations take proactive measures to protect sensitive data and comply with regulatory standards. Features often include:
- Vulnerability Scans: Identify potential weaknesses in systems that could expose PHI.
- Risk Scoring: Prioritize risks based on their potential impact on PHI security.
- Mitigation Strategies: Provide recommendations for addressing identified risks.
Key Features to Look for in PHI-Finding Software:
When selecting software to find and protect PHI, consider the following features:
- Automated Scanning: The ability to automatically scan and identify PHI across multiple data sources, including cloud storage, on-premises systems, and mobile devices.
- Real-Time Alerts: Notifications for potential data breaches or unauthorized access to sensitive information, allowing for quick response and remediation.
- Compliance Reporting: Tools to generate reports demonstrating compliance with HIPAA and other regulations, aiding in audits and assessments.
- User Access Controls: Features that restrict access to PHI based on user roles, ensuring that only authorized personnel can view sensitive data.
- Data Encryption: Ensuring that data at rest and in transit is encrypted to prevent unauthorized access.
Best Practices for Implementing PHI-Finding Software:
To effectively utilize software that finds PHI, organizations should follow these best practices:
- Conduct a Needs Assessment: Evaluate your organization’s specific requirements for PHI management and compliance to choose the right software.
- Involve Key Stakeholders: Engage IT, compliance officers, and clinical staff in the selection and implementation process to ensure the software meets everyone’s needs.
- Provide Training: Offer comprehensive training for staff on how to use the software and understand the importance of safeguarding PHI.
- Regularly Review Policies: Continuously update and review policies and procedures regarding PHI handling to ensure compliance with evolving regulations.
- Monitor and Audit: Regularly monitor access to PHI and conduct audits to identify any potential vulnerabilities or non-compliance issues.
FAQ’s
Here are five FAQs with short answers related to software that can find protected health information (PHI):
1. What is protected health information (PHI)?
PHI is any individually identifiable health information related to a patient’s medical history, treatment, or payment that is protected under regulations like HIPAA.
2. Why is it important to find PHI?
Finding PHI is crucial for regulatory compliance, preventing data breaches, and maintaining patient trust, ensuring sensitive information is handled securely.
3. What types of software can identify PHI?
Common types of software that can find PHI include Data Loss Prevention (DLP) tools, Electronic Health Record (EHR) systems, compliance management software, data discovery tools, and risk assessment tools.
4. How can I ensure my PHI-finding software is effective?
Look for features like automated scanning, real-time alerts, compliance reporting, user access controls, and data encryption to ensure effective protection of PHI.
5. What are the best practices for implementing PHI-finding software?
Best practices include conducting a needs assessment, involving key stakeholders, providing training, regularly reviewing policies, and monitoring access to PHI.
Conclusion
In conclusion, utilizing software that can find and protect Protected Health Information (PHI) is essential for healthcare organizations to ensure compliance and safeguard sensitive data. By selecting the right tools and following best practices, organizations can enhance their data protection strategies, mitigate risks, and maintain patient trust. Ultimately, effective PHI management contributes to improved operational efficiency and better healthcare outcomes.