In today’s fast-paced IT environment, effective management of software assets is vital for security and compliance. Tenable, a leader in vulnerability management, can indeed perform software inventory, providing organizations with visibility into their software landscape, helping manage vulnerabilities, and ensuring compliance with industry standards.
“Yes, Tenable can perform software inventory. It helps identify installed software across systems, allowing organizations to monitor vulnerabilities and manage assets more effectively.”
In this article, We will discuss “can tenable do software inventory “
What Is Software Inventory?
Before we look at how Tenable performs software inventory, it’s important to understand what software inventory entails. Software inventory is the process of identifying and cataloging all software applications installed across an organization’s systems, including operating systems, third-party software, and custom applications.
This inventory allows organizations to maintain visibility over software usage, track updates, ensure license compliance, and identify unauthorized or outdated software that could pose security risks.
In short, software inventory is foundational to any effective IT asset management (ITAM) and cybersecurity strategy.
Can Tenable do Software Inventory:
Also Read: What Is Testing In Zillexit Software – Explained Simply!
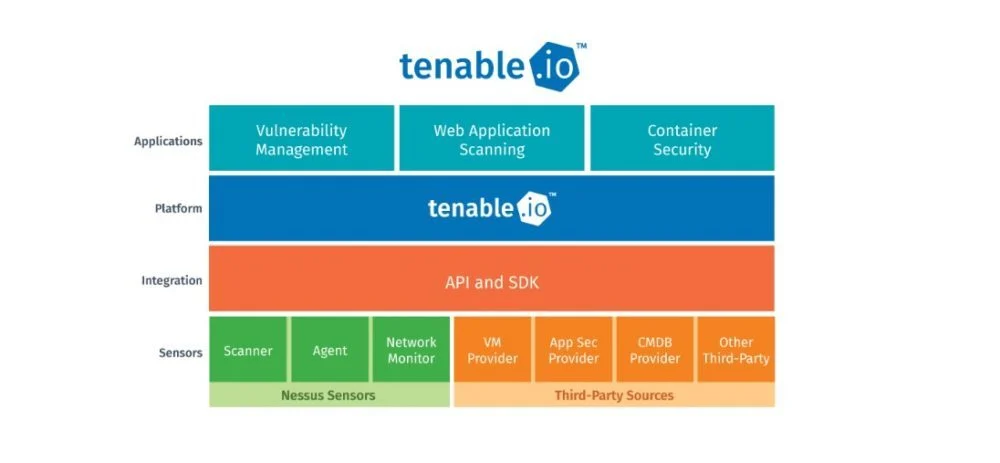
Yes, Tenable can assist with software inventory management. Tenable’s solutions, such as Tenable.io and Tenable.sc, provide visibility into the software assets across an organization’s network. Through vulnerability management and scanning, it identifies installed software, track versions, and helps detect unauthorized or outdated software. This feature is crucial for maintaining security hygiene, ensuring compliance, and mitigating risks associated with unpatched software. Tenable’s tools integrate with other asset management systems for more comprehensive software inventory and vulnerability management.
Tenable Software Inventory:
Tenable offers robust software inventory capabilities through its solutions like Tenable.io and Tenable.sc. By using active and passive scanning methods, Tenable detects and catalogs all installed software across devices and networks, including versions and configurations. This inventory process helps organizations manage vulnerabilities, track licensing, and ensure compliance.
Additionally, Tenable integrates vulnerability management with software inventory, alerting administrators about outdated or unauthorized software. With continuous monitoring and detailed reporting, Tenable enables better asset management and strengthens an organization’s overall security posture.
How Tenable Performs Software Inventory:
Tenable’s platforms, including Tenable.io, Tenable.sc, and Nessus, come equipped with tools that provide comprehensive software inventory capabilities. These tools allow organizations to discover and monitor all installed software across endpoints, servers, and network devices. Here’s a detailed look at how Tenable handles software inventory:
1. Automated Discovery of Installed Software:
Tenable uses active and passive scanning techniques to detect installed software on all devices connected to your network. This discovery includes all operating systems, applications, plugins, and browser extensions, providing a complete picture of your software environment.
- Active Scanning : Tenable’s Nessus scanner actively probes devices to detect installed software, including software versions, configurations, and license details.
- Passive Monitoring : For continuous monitoring, Tenable’s Passive Vulnerability Scanner (PVS) captures network traffic and identifies software and services being used across the environment.
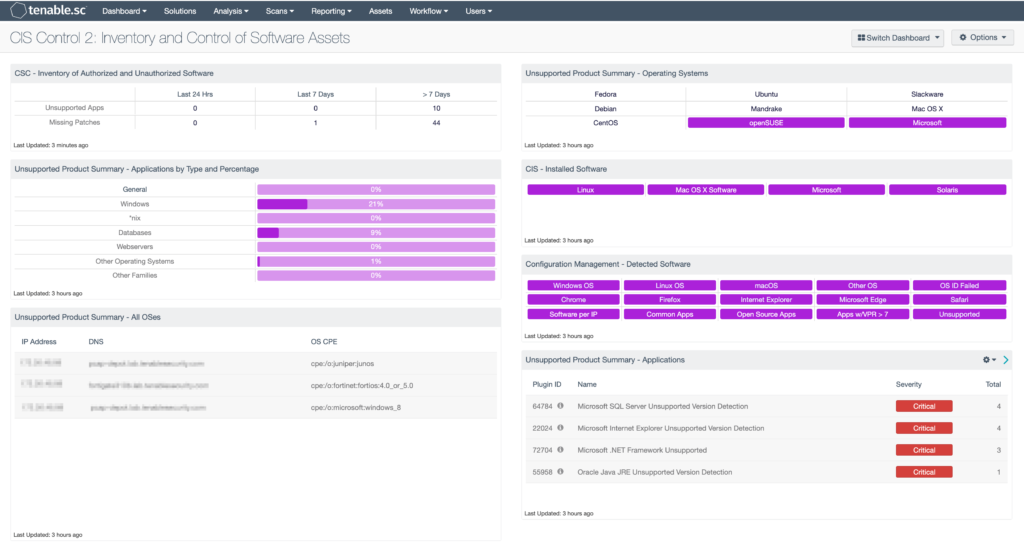
2. Detailed Software Inventory Reports:
Once Tenable identifies the software, it generates detailed software inventory reports. These reports allow IT administrators to:
- Track Software Versions: Ensure that the most recent and secure versions of software are installed.
- Detect Unauthorized Software: Spot unapproved applications or software that may introduce vulnerabilities.
- Monitor Licensing Compliance: Keep track of license usage and ensure that software licenses are not being violated.
3. Vulnerability Assessment Linked to Software Inventory:
One of Tenable’s strengths lies in its ability to integrate vulnerability assessment with software inventory. Not only does Tenable catalog installed software, but it also assesses whether these applications have known vulnerabilities. This gives organizations a prioritized list of issues to address, helping them focus on high-risk software that needs updates or patches.
For example, if Tenable detects an outdated version of a popular web server software, it will cross-reference it with known vulnerabilities in its database, immediately flagging potential security risks.
Also Read: Is There Chromebook Software To Program A Midland Mxt105 – A Detailed Overview!
4. Asset Tagging and Management:
Tenable allows users to tag software assets based on various criteria, such as department, business unit, or software type. This helps in organizing software inventory and identifying critical applications that require frequent monitoring.
5. Continuous Monitoring and Alerts:
Tenable provides continuous monitoring of your software environment. It sends alerts when new software is installed, when existing software becomes outdated, or when unauthorized software appears on the network. This ensures that organizations maintain real-time visibility over their software assets.
Why Software Inventory Matters for Cybersecurity:
A robust software inventory is a critical component of any cybersecurity strategy. Here’s why:
- Prevents Security Breaches : Unpatched software is one of the most common entry points for cyberattacks. Tenable helps organizations identify outdated software and alerts them to vulnerabilities that need immediate attention.
- Eliminates Shadow IT : Unauthorized software, often referred to as “shadow IT,” can pose serious security risks. Tenable helps detect unapproved software before it becomes a problem.
- Ensures Compliance : Many industry regulations, such as PCI DSS, HIPAA, and GDPR, require organizations to maintain a current software inventory as part of their compliance efforts. Tenable helps organizations meet these regulatory requirements by providing comprehensive software visibility.
- Improves License Management : Keeping track of software licenses can be challenging, especially for large organizations. Tenable’s software inventory feature helps IT departments avoid license violations and unexpected costs by keeping an accurate record of all installed software.
Key Benefits of Tenable’s Software Inventory Capabilities:
Tenable’s ability to perform software inventory provides several key benefits for organizations:
1. Improved Security Posture:
By providing real-time visibility into installed software, Tenable helps organizations quickly identify security risks such as unpatched vulnerabilities, outdated software, and unauthorized installations. This significantly reduces the attack surface and helps maintain a strong security posture.
2. Streamlined Compliance:
With detailed software inventory reports, organizations can easily demonstrate compliance with industry regulations and internal security policies. This helps avoid penalties and ensures adherence to best practices in security management.
Also Read: How To Delete An Epomaker Software Account – An Easy Guide!
3. Efficient Asset Management:
Tracking software across a large organization can be overwhelming without the right tools. Tenable’s software inventory capabilities help IT departments manage their software assets efficiently, reducing time spent on manual processes and ensuring that all software is accounted for.
4. Actionable Insights:
Tenable not only identifies software but also provides actionable insights based on the software’s risk profile. For instance, if a critical vulnerability is detected in a specific version of software, Tenable will alert administrators and offer remediation steps, such as applying patches or updating to a newer version.
How Tenable’s Software Inventory Stands Out:
Tenable stands out from other software inventory tools for several reasons:
- Integration with Vulnerability Management : Unlike standalone software inventory tools, Tenable combines inventory capabilities with vulnerability management, offering a more comprehensive solution for security teams.
- Scalability : Whether you’re a small organization or a large enterprise, Tenable can scale to meet your software inventory needs, with support for thousands of assets across multiple environments.
- Ease of Use : Tenable’s interface is intuitive, making it easy for IT and security teams to navigate reports, manage assets, and take action on identified risks.
- Automation and Continuous Monitoring : Tenable provides automated scans and continuous monitoring, ensuring that your software inventory is always up-to-date without manual intervention.
FAQ’s
1. Can Tenable perform software inventory?
Yes, Tenable can perform software inventory by scanning devices and networks to identify installed software across your environment.
2. How does Tenable’s software inventory work?
Tenable uses active and passive scanning to detect installed software, providing detailed reports on software versions, configurations, and vulnerabilities.
3. Does Tenable track software vulnerabilities?
Yes, Tenable not only inventories software but also assesses vulnerabilities, helping you prioritize patching and updates.
4. Can Tenable help with software license management?
Yes, Tenable provides visibility into installed software, helping organizations track licenses and ensure compliance with usage policies.
5. Does Tenable support continuous monitoring of software inventory?
Yes, Tenable offers continuous monitoring and alerts for changes in software installations or configurations, ensuring up-to-date inventory data.
6. How does Tenable detect unauthorized software?
Tenable uses automated discovery methods to identify all installed software and flags any unapproved or unauthorized applications, helping organizations avoid security risks.
7. Can Tenable integrate with other asset management systems?
Yes, Tenable integrates seamlessly with other asset management systems, providing a more comprehensive approach to software inventory and vulnerability management.
8. Is Tenable suitable for both small and large organizations?
Yes, Tenable is scalable and can support organizations of any size, from small businesses to large enterprises, ensuring efficient software inventory management across different environments.
Conclusion
Tenable effectively performs software inventory by identifying and cataloging installed software across your network, providing valuable insights into vulnerabilities and compliance. Its combination of automated discovery, continuous monitoring, and integrated vulnerability assessment enhances security and asset management. Overall, Tenable is a powerful tool for maintaining a secure and up-to-date software inventory.